Spam bots submitted over 99 billion junk form entries across the web in 2024. Your site caught some of that traffic, guaranteed. The best tactics for form spam prevention combine…
Table of Contents
Your inbox fills with garbage daily. Fake inquiries, promotional spam, and bot-generated nonsense drown out legitimate customer messages.
WordPress contact forms attract automated spam like magnets, wasting hours of sorting time and corrupting your lead data. Most sites receive 50-200 spam submissions weekly without protection.
This guide shows you how to stop spam from WordPress contact forms using proven methods that block 95%+ of unwanted submissions. You’ll learn which plugins work best, how to configure CAPTCHAs correctly, and advanced techniques that layer multiple defenses.
No technical expertise required.
What is WordPress Contact Form Spam?
WordPress contact form spam consists of automated bot submissions and unwanted messages sent through website forms that waste time, fill databases with junk data, and can harm site performance.
Spam bots target unprotected forms using automated scripts to submit fake entries. These submissions clog your inbox, corrupt analytics data, and consume server resources.
Real businesses lose hours sorting through junk messages daily. Some sites receive hundreds of spam entries per week without proper protection.
Types of WordPress Contact Form Spam
| Spam Type | Attack Method | Primary Intent | Detection Difficulty |
|---|---|---|---|
| Bot-generated submissions | Automated script execution filling form fields programmatically | Mass distribution of links or promotional content | Low (detectable via CAPTCHA and honeypot fields) |
| SEO link spam | Inserting backlinks in message fields for link-building | Manipulating search rankings through artificial backlinks | Low to Medium (link patterns are identifiable) |
| Email harvest spam | Submitting fake entries to collect recipient email addresses | Building email lists for future spam campaigns | Medium (requires monitoring submission patterns) |
| Fake quote/offer spam | Requesting business quotes with fraudulent information | Wasting business resources or testing form vulnerabilities | Medium to High (appears as legitimate inquiry) |
| Phishing attempts | Posing as legitimate entity to extract sensitive data | Stealing credentials, financial information, or personal data | High (sophisticated social engineering tactics) |
| Malware or scam URL submissions | Embedding malicious links in form submissions | Infecting systems or redirecting to fraudulent websites | Medium (URL scanning tools detect known threats) |
| Form field injection attempts | Inserting SQL queries or script code into input fields | Exploiting database vulnerabilities or executing XSS attacks | Low (input sanitization catches most attempts) |
| Human-generated promo spam | Manual submission of promotional messages by individuals | Advertising services or products to business owners | High (legitimate user behavior with marketing intent) |
| Newsletter sign-up spam via forms | Using contact forms to subscribe random emails to lists | Email bombing or harassing targeted email addresses | Medium (double opt-in verification prevents most) |
| Spam sent via unsecured form APIs | Exploiting unprotected API endpoints for bulk submissions | Bypassing front-end security to automate spam delivery | Low to Medium (API rate limiting blocks mass requests) |
Bot-Generated Spam
Automated bots scan the internet looking for vulnerable forms. They fill out fields with random text, promotional links, or malicious content.
Most spam submissions come from bots using scripts that detect standard form field names like “email” or “message.” These scripts submit forms repeatedly across thousands of sites.
Human Spam Submissions
Real people manually submit promotional messages, link requests, or commercial offers. They’re harder to block because they behave like legitimate users.
These spammers often target specific industries or high-traffic sites. They leave messages with backlinks hoping to boost their own SEO rankings.
Brute Force Form Attacks
Attackers submit forms hundreds or thousands of times to overwhelm your server, test for vulnerabilities, or inject malicious code into your database.
The submission frequency spikes dramatically during these attacks. Your site slows down and may crash if the attack is severe enough.
Why WordPress Forms Attract Spam
Default Form Vulnerability
Most WordPress forms ship without spam protection enabled. Bots exploit this gap within hours of a form going live.
Unprotected contact forms are easy targets. They have predictable field names, no verification steps, and accept any submission without question.
Lack of Verification Methods
Forms without CAPTCHA, email verification, or honeypot fields can’t distinguish between humans and bots.
Spammers prefer sites with weak form security because they can automate thousands of submissions daily. Your form becomes part of their rotation.
Install Anti-Spam Plugins
Akismet Configuration
Akismet filters spam using a massive database of known spam patterns and IP addresses. It checks every submission against this database in real-time.
Get your API key from WordPress.com, install the plugin, then paste the key in settings. Takes under five minutes.
Akismet catches roughly 99.8% of automated spam but occasionally flags legitimate messages. Check your spam folder weekly for false positives.
reCAPTCHA Implementation
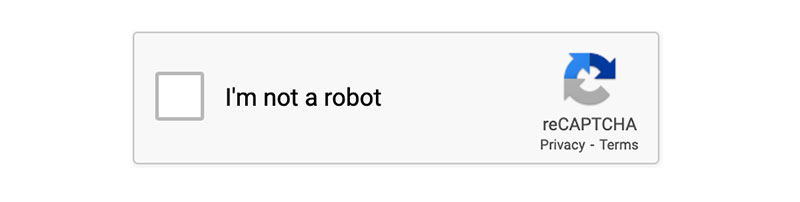
Google reCAPTCHA adds a verification layer that bots struggle to bypass. Version 3 runs invisibly and assigns each visitor a score between 0.0 (bot) and 1.0 (human).
Register your site at google.com/recaptcha to get site and secret keys. Most WordPress contact form plugins have built-in reCAPTCHA fields you just paste these keys into.
Set your threshold around 0.5 for balanced protection. Lower scores block more bots but risk blocking real users on VPNs or shared networks.
CleanTalk Integration
CleanTalk operates entirely in the cloud without showing CAPTCHAs to visitors. It analyzes visitor behavior, email addresses, and submission patterns.
The plugin checks submissions against a database of 1.5 billion spam records. It blocks suspicious entries before they hit your inbox.
CleanTalk requires a paid subscription but eliminates the friction of visible CAPTCHAs. Good for sites where form conversions matter more than free tools.
Honeypot Anti-Spam
Honeypots add invisible fields to your form using CSS. Humans never see these fields, but bots auto-fill everything.
When a submission includes data in the honeypot field, you know it’s a bot. The form rejects it instantly.
This method is free, works on all types of forms, and doesn’t annoy legitimate users. It catches unsophisticated bots but misses smarter ones that check for hidden fields.
Configure Built-in Form Protection
Contact Form 7 Spam Protection
Contact Form 7 includes basic spam filters but requires manual configuration. Add Akismet integration or reCAPTCHA tags to your form template.
Insert the quiz field for simple questions like “What is 2+2?” Bots fail these consistently.
Enable the acceptance checkbox requiring users to agree to terms. This adds one more step bots often skip.
WPForms Spam Settings
WPForms has a dedicated spam protection panel under form settings. Toggle on honeypot, enable reCAPTCHA, and activate custom keyword filtering.
The plugin blocks entries containing blacklisted terms or suspicious patterns. You define these keywords based on spam you’ve received.
Entry limiting restricts how many submissions one IP address can make per hour.
Gravity Forms Security Options
Gravity Forms offers conditional logic to hide forms until users complete preliminary actions. Pair this with reCAPTCHA fields and custom validation rules.
Set up notification filters to quarantine suspicious entries rather than deleting them outright. Review these weekly to catch patterns.
The plugin supports custom anti-spam hooks if you want to write PHP functions for advanced filtering.
Add CAPTCHA to Contact Forms
reCAPTCHA v2 Setup
Register your site at google.com/recaptcha/admin, select v2 checkbox, add your domain, then copy the site and secret keys. Paste these keys into your form plugin’s CAPTCHA settings.
The checkbox appears above your submit button asking users to verify they’re human. Bots can’t solve the image challenges that sometimes follow.
reCAPTCHA v3 Implementation
Version 3 runs invisibly and scores every visitor from 0.0 to 1.0 based on behavior patterns. Set your threshold at 0.5 initially, then adjust based on false positives.
Lower thresholds (0.3) block more aggressively but may catch legitimate users. Higher thresholds (0.7) let more through but reduce friction on lead generation forms.
Each form action gets its own score, so you can set different thresholds for contact vs. registration submissions.
hCaptcha Alternative
hCaptcha offers similar protection without sending data to Google. Privacy-focused sites prefer it.
Setup works identically to reCAPTCHA. Get keys from hcaptcha.com, paste them in your plugin, done.
Cloudflare users get hCaptcha integration automatically through their dashboard.
Enable Email Verification
Double Opt-in Implementation
Send a confirmation email with a unique verification link after form submission. Only process entries after users click that link.
This kills bot submissions instantly since bots can’t access email inboxes. Your database stays clean and every entry is verified human.
Most form plugins support this through add-ons or built-in settings. WPForms and Gravity Forms have native double opt-in fields.
Email Domain Validation
Block disposable email services like tempmail.com or 10minutemail.net by checking submissions against a blacklist of temporary domains.
Use plugins like Stop Spammers or add custom validation code that checks the domain portion of submitted emails. Reject entries from known disposable providers.
Check MX records to verify the email domain actually has mail servers configured.
Block Spam by IP Address
Manual IP Blocking
Add problematic IPs to your .htaccess file or use your security plugin’s blocklist. Check your spam submissions for repeat offenders and ban them permanently.
Edit .htaccess in your root directory:
order allow,deny
deny from 123.45.67.89
allow from all
Works immediately but requires manual updates as spammers rotate IPs.
Automatic IP Blocking
Wordfence and Sucuri automatically block IPs after multiple failed submissions or suspicious behavior. Set your threshold at 5-10 attempts per hour.
These plugins maintain shared blacklists across thousands of sites. An IP flagged on other sites gets blocked on yours too.
Rate limiting prevents single IPs from overwhelming your forms while allowing legitimate users through.
Implement Rate Limiting
Submission Frequency Limits
Restrict submissions to one per IP address every 60 seconds. Humans rarely submit forms faster than this, but bots do.
Add this check at the form processing level using plugin settings or custom code. Store the last submission timestamp per IP in your database.
Most quality plugins include this feature. Enable it and set appropriate cooldown periods based on your form type.
Throttling Configuration
Configure your web server to limit requests from single IPs. Nginx’s limit_req module or Apache’s mod_evasive work well.
Set burst allowances for legitimate traffic spikes while blocking sustained floods. A burst of 10 requests is reasonable, anything beyond triggers blocks.
Add Custom Validation Rules
Field-Level Validation
Require specific formats for email, phone, and other fields using regex patterns. Block entries with obviously fake data.
Email regex: ^[a-zA-Z0-9._%+-]+@[a-zA-Z0-9.-]+\.[a-zA-Z]{2,}$
Phone validation prevents entries like “1111111111” or “0000000000” that bots commonly use.
Content Filtering Rules
Scan message fields for spam keywords like “casino,” “viagra,” “crypto,” or excessive links. Auto-reject submissions containing 3+ URLs.
Build your blacklist based on actual spam you receive. Patterns emerge quickly.
Some spammers use character substitutions (v1agra). Use fuzzy matching or pattern detection to catch variations.
Geographic Restrictions
Block entire countries if your business only serves specific regions and spam comes from elsewhere. GeoIP databases identify visitor locations by IP address.
Wordfence lets you block by country in the firewall settings. Useful if 90% of your spam originates from specific regions you don’t serve.
Be cautious with VPN users who appear to come from blocked countries.
Configure Firewall Protection
Wordfence Firewall Setup
Install Wordfence, run the setup wizard, then enable the Web Application Firewall in extended protection mode. This requires adding code to wp-config.php for early loading.
The firewall blocks malicious requests before they reach WordPress. It updates rules automatically as new threats emerge.
Enable real-time threat defense for immediate protection against zero-day exploits targeting form vulnerabilities.
Sucuri Security Configuration
Sucuri’s cloud-based WAF filters traffic before it hits your server. Sign up for their firewall service, update your DNS to route through their network, configure your security level.
Choose paranoid mode for maximum protection or moderate for balanced filtering. Virtual patching protects against known WordPress vulnerabilities even if you haven’t updated yet.
Cloudflare Integration
Point your nameservers to Cloudflare, then enable bot management and challenge pages in the firewall section. Free tier includes basic protection, paid plans add advanced bot detection.
Set security level to medium initially. High blocks aggressively but may challenge legitimate users.
Cloudflare’s challenge duration determines how long verified users can browse without re-verification. Set it to 4-8 hours for best balance.
Use Time-Based Restrictions
Minimum Time Requirements
Track how long users view your form before submitting. Reject submissions made in under 3 seconds since humans can’t read and complete forms that fast.
Add a hidden timestamp field when the form loads, then compare it to submission time server-side. Bots submit instantly, humans take 10+ seconds minimum.
Maximum Time Limits
Expire form sessions after 30 minutes to prevent bots from holding sessions open. Generate a unique token when the form loads and validate it expires after your time limit.
This stops bots that load forms, wait, then submit later to avoid time-minimum checks.
Add Quiz or Math Questions
Simple Math CAPTCHA
Add a field asking “What is 7 + 3?” with the answer validated server-side. Rotate questions randomly so bots can’t hardcode answers.
Keep math simple (single-digit addition) so legitimate users don’t struggle. Still effective against most bots.
Works better than image CAPTCHAs for mobile forms since typing is easier than selecting images on small screens.
Custom Question Fields
Ask site-specific questions like “What city is our office located in?” that only legitimate visitors would know.
Adjust questions based on your audience. B2B sites can ask industry terms, local businesses can ask location questions.
Enable WordPress Comment Blacklist
Common Spam Keywords
Navigate to Settings > Discussion > Disallowed Comment Keys and add spam terms. These rules apply to contact forms using WordPress’s native filtering.
Add one keyword per line. Include common spam phrases you’ve seen repeatedly.
Update this list monthly as spam patterns evolve. Spammers rotate keywords to evade filters.
URL Pattern Blocking
Limit messages to 2 links maximum. Most legitimate contact form messages contain zero or one link.
Block specific TLDs frequently used by spammers (.tk, .ml, .ga) if you never need to receive messages from those domains.
Monitor Form Submissions
Submission Logging
Enable entry storage in your form plugin to review all submissions. WPForms and Gravity Forms save entries in your WordPress database automatically.
Set retention policies to auto-delete entries after 90 days if you don’t need permanent records. Keeps your database lean.
Notification Configuration
Configure admin emails to receive alerts for new submissions. Add multiple recipients if your team needs visibility.
Set up separate notifications for different contact forms so the right person sees relevant entries.
Filter notifications by entry source or specific field values using conditional logic.
Analytics Integration
Track form submissions as Google Analytics events to measure spam rates and legitimate conversion patterns. Name your events clearly: “form_submission_contact” or “form_submission_quote.”
Monitor completion rates to spot spam floods. Sudden spikes in submissions with low completion times indicate bot attacks.
Database Cleanup
Remove Spam Entries
Delete spam entries in bulk from your form plugin’s entries page. Most plugins let you filter by status, date, or content.
Run cleanup monthly to prevent database bloat. Large entry tables slow down your admin panel.
Back up your database before bulk deletions in case you accidentally remove legitimate entries.
Optimize Form Tables
Run database optimization quarterly using plugins like WP-Optimize or direct MySQL commands. This defragments tables and rebuilds indexes.
Form entry tables grow quickly on high-traffic sites. Optimization reclaims wasted space and speeds up queries.
Advanced Protection Methods
JavaScript Validation
Require JavaScript to be enabled for form submission. Add a hidden field that JavaScript populates with a value, then reject submissions where that field is empty.
Most bots don’t execute JavaScript properly. Catches basic scrapers instantly.
Consider accessibility. Some users with screen readers may have limited JavaScript support.
Token-Based Verification
Generate a unique CSRF token when rendering the form, store it in the user’s session, then validate the token matches on submission.
Tokens expire after your session timeout period. Prevents bots from reusing old forms.
WordPress nonces serve this purpose. Use wp_nonce_field() when building custom forms.
Hidden Field Techniques
Add multiple honeypot fields with names like “website,” “url,” or “company” that look legitimate to bots. Position them off-screen using CSS.
Bots auto-fill these thinking they’re required. Legitimate users never see or interact with them.
Combine with timestamp fields and JavaScript validation for layered protection.
Test Your Spam Protection
Manual Testing Procedure
Submit test entries through your form to verify legitimate submissions work correctly. Try different devices, browsers, and networks.
Test with and without JavaScript enabled. Verify CAPTCHA appears and validates properly.
Check that confirmation emails arrive, admin notifications fire, and entries save correctly in your database.
Load Testing
Use tools like Apache Bench or JMeter to simulate multiple rapid submissions. Verify your rate limiting kicks in at the right thresholds.
Submit 20-30 forms in quick succession from the same IP. Confirm the system blocks excess attempts while allowing reasonable use.
Monitor server resources during tests to ensure protection doesn’t crash your site under legitimate load.
Common Mistakes to Avoid
Making CAPTCHA too difficult reduces legitimate conversions by 30-40%. Balance security with user experience.
Blocking entire countries without data to justify it. Check where your real customers come from first.
Not monitoring false positives. Review spam folders weekly or you’ll miss legitimate inquiries.
Ignoring mobile users. Touch-based CAPTCHAs are harder on phones than desktops.
Setting rate limits too low. Some legitimate users need to submit corrections immediately after initial submissions.
Using only one protection method. Layer multiple techniques since no single method catches everything.
FAQ on WordPress Contact Forms Spam
Does reCAPTCHA really stop spam bots?
reCAPTCHA blocks 95-99% of automated spam when configured correctly. Version 3 works invisibly by scoring visitor behavior patterns from 0.0 to 1.0, while v2 shows checkbox challenges. Set thresholds around 0.5 for balanced protection without blocking legitimate users.
Which is better, Akismet or reCAPTCHA?
Akismet excels at content-based filtering using spam pattern databases, while reCAPTCHA focuses on behavioral verification. Best results come from using both together since they catch different spam types. Akismet requires an API key, reCAPTCHA needs site registration.
Can I stop spam without annoying real users?
Yes. Honeypot fields, invisible reCAPTCHA v3, and time-based validation work silently behind the scenes. These methods catch bots without adding friction to legitimate submissions. Avoid aggressive visible CAPTCHAs that reduce form conversions by 30-40%.
How do honeypot fields work?
Honeypots add hidden fields using CSS that humans never see but bots auto-fill. When a submission includes data in these invisible fields, you know it’s automated and reject it instantly. Works on all WordPress forms without user interaction required.
Should I block countries to reduce spam?
Only if your business serves specific regions and data shows spam originates elsewhere. Geographic blocking using GeoIP databases stops regional bot networks but may block VPN users or legitimate international visitors. Review spam sources before implementing country restrictions.
What’s the best free anti-spam plugin?
Akismet handles millions of sites and catches most automated spam at no cost for personal blogs. For paid sites, combine free honeypot plugins with reCAPTCHA integration. Contact Form 7 and WPForms include built-in honeypot and reCAPTCHA support.
How often should I clean spam entries from my database?
Monthly cleanup prevents database bloat on high-traffic sites. Most form plugins let you bulk delete spam entries by date or status. Set automatic deletion after 90 days if you don’t need permanent records of rejected submissions.
Can spam damage my WordPress site?
Excessive spam submissions slow server performance, inflate database size, and can trigger hosting resource limits. Brute force attacks via forms may expose vulnerabilities or crash sites under load. Security plugins like Wordfence block malicious requests before they reach WordPress.
Why am I still getting spam with CAPTCHA enabled?
Some sophisticated bots solve CAPTCHAs using AI or human farms. Layer multiple protection methods like honeypots, rate limiting, and email verification for comprehensive defense. Also check your CAPTCHA threshold settings aren’t too lenient.
Does blocking IPs actually work against spam?
Temporarily. Individual spammers stay blocked, but organized spam operations rotate through thousands of IPs. Automatic IP blocking through Wordfence or Sucuri works better than manual lists since they update continuously based on global threat data and suspicious behavior patterns.
Conclusion
Learning how to stop spam from WordPress contact forms protects your time, database integrity, and server resources. No single method blocks everything, so layer multiple defenses.
Start with Akismet and reCAPTCHA for immediate 95%+ spam reduction. Add honeypot fields and rate limiting for deeper protection against sophisticated bots.
Monitor your spam folders weekly to catch false positives. Adjust CAPTCHA thresholds and validation rules based on actual attack patterns you observe.
Most sites see dramatic spam drops within 48 hours of implementing these techniques. Your inbox stays clean, legitimate inquiries reach you instantly, and you reclaim hours wasted sorting junk submissions.
Configure protection once, then forget about spam.